Decrypt wireless frames with Wireshark
- #wireless
- #security
Components Used
- A computer running any OS like; Linux, MacOS, or Windows.
- Packet analyzer Wireshark
- Previous packets capture collected in monitor mode
- Know the password of the target SSID
Considerations
- Up to 64 keys are supported.
- The packets captured collected must contain the 4-way handshake (EAPOL-Messages 1 to 4), the Wireshark decrypt tool uses WPA/WPA2 keys derived from an EAPOL handshake.
In other words, if your capture doesn’t contain the complete handshake, Wireshark won’t be able to decrypt the frames it won’t work using control frames, management frames, and data frames only.
How to
Wireshark is a powerful tool that can decrypt 802.11 frames using the corresponding password from a specific SSID. It can decrypt WEP, WPA/WPA2, and TKIP.
In this post, we are going to focus only on WPA2-PWD & WPA2-PSK.
- Open your .pcap file collected with Wireshark. (I filtered only interesting traffic for this post)
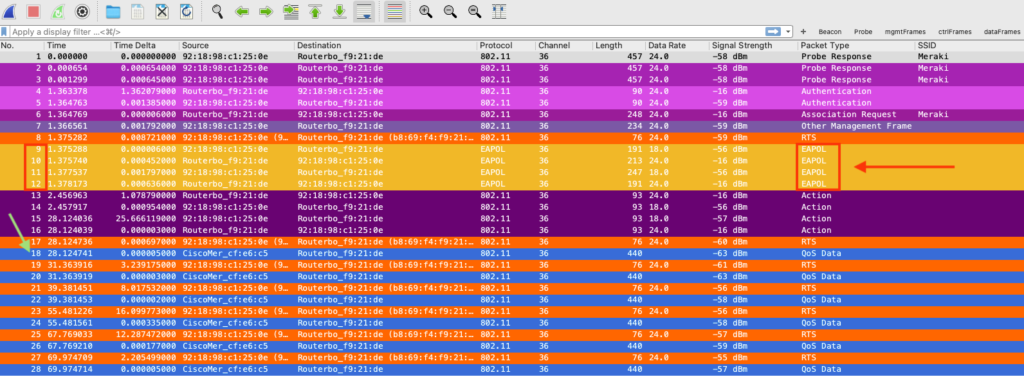
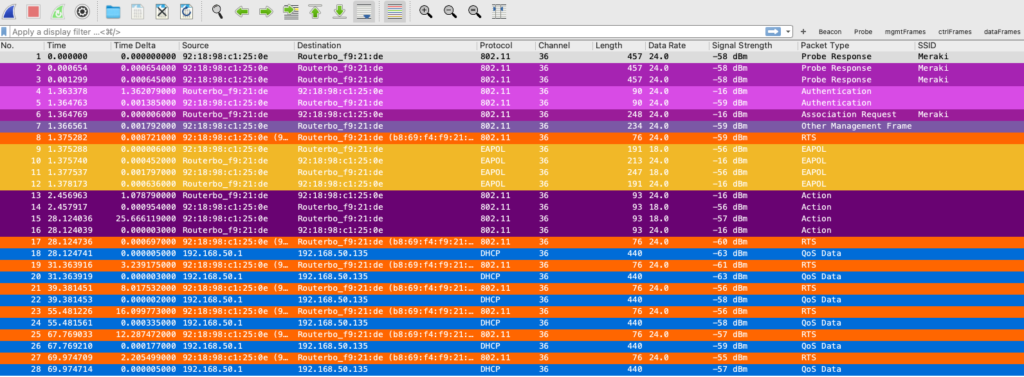
From packets 9 – 12 we can see the 4-way handshake required, packets 18, 20, 22, and so on shows encrypted Data.
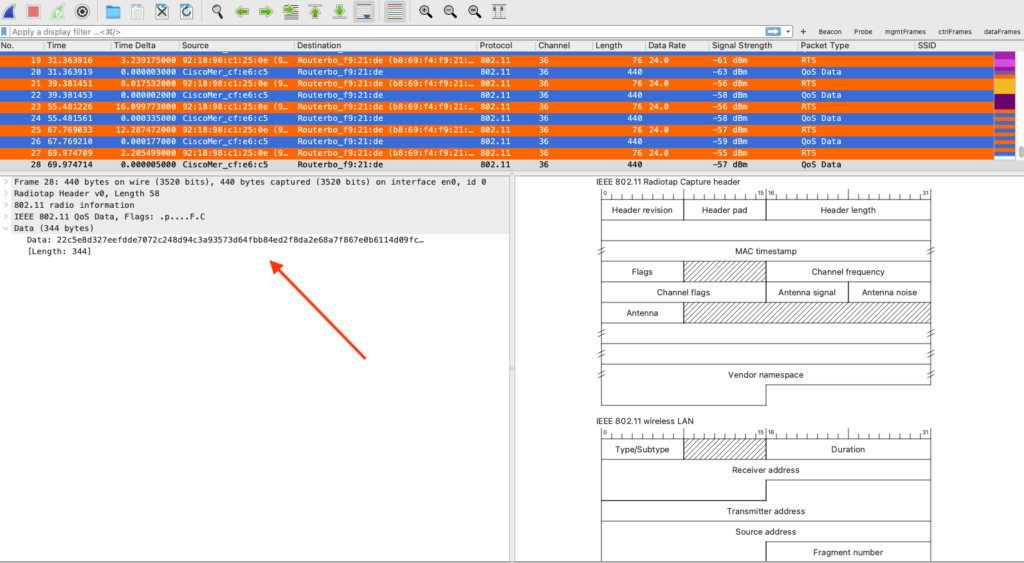
Let’s take a look at frame 28, see the payload is encrypted.
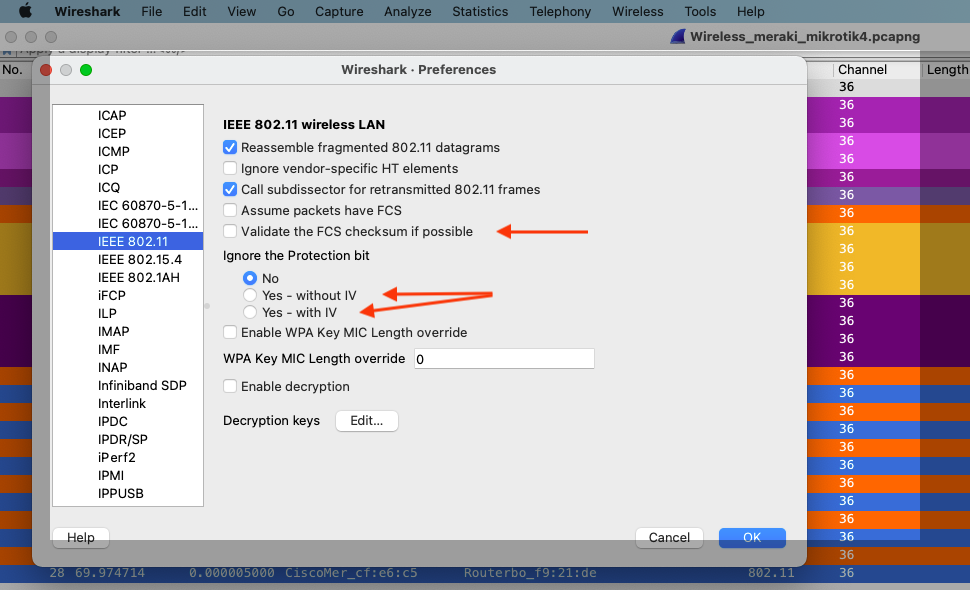
- Go to the Wireshark tab > Preferences > Protocols > IEEE 802.11, as shown in the image:
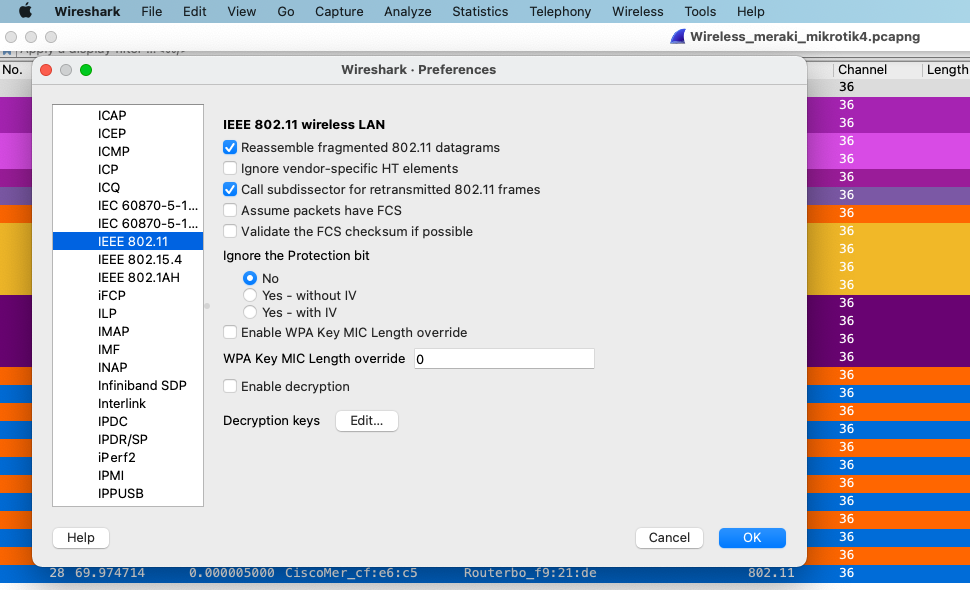
- Enable decryption and click on Edit, as shown in the image:
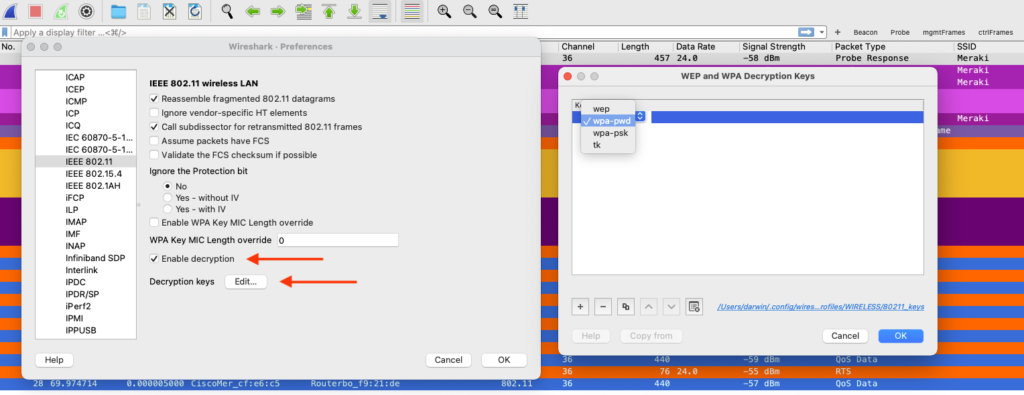
- Let’s start with wpa-psw, the key is in plaintext, and the password goes first followed by
:and the name of the SSID, as shown in the image.
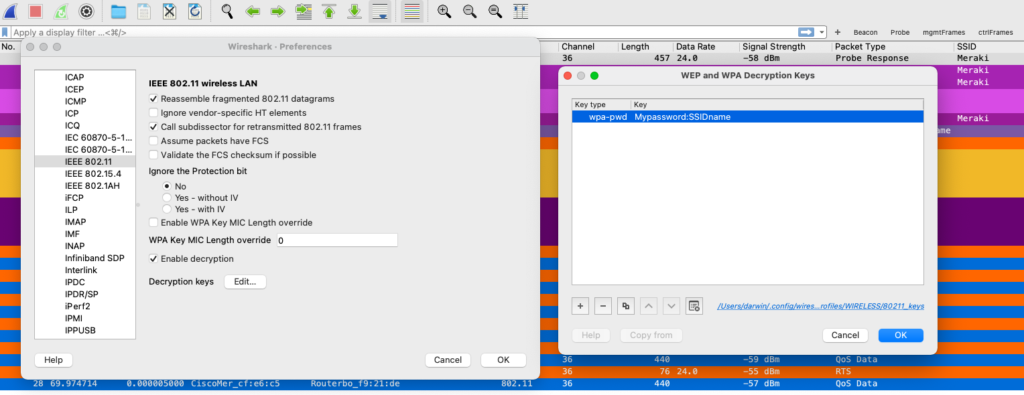
- To use wpa-psk you will need to derive your PSK combining your passphrase and your SSID name, you can use this link for simplicity, copy and paste the result in Wireshark, as shown in the images.
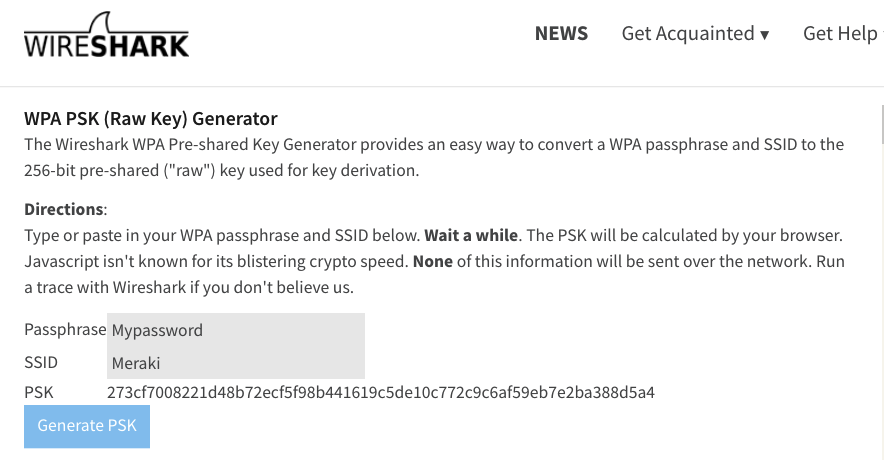
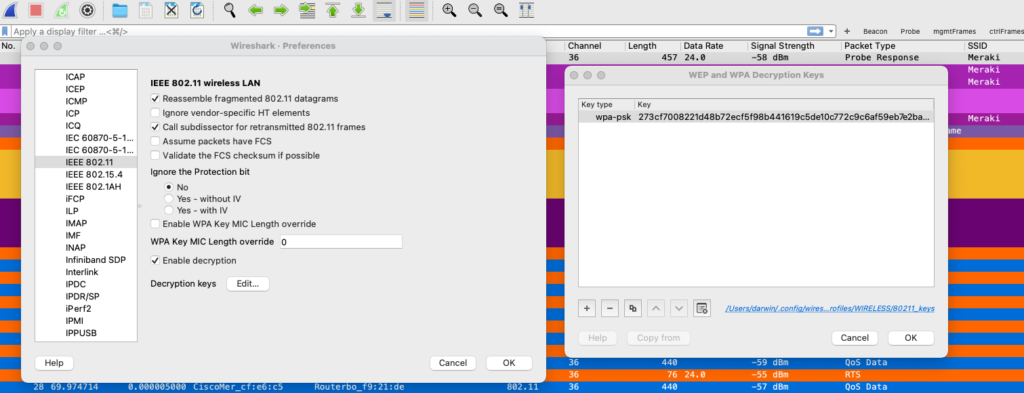
In my case, the name of the SSID is “Meraki”
- Click OK.
Let’s see packets 18, 20, and 22 again! Now, we can see L3 information followed by the protocol of the data which is DHCP (before we had 802.11 and L2 information only)
Let’s take a look at frame 28 one more time!
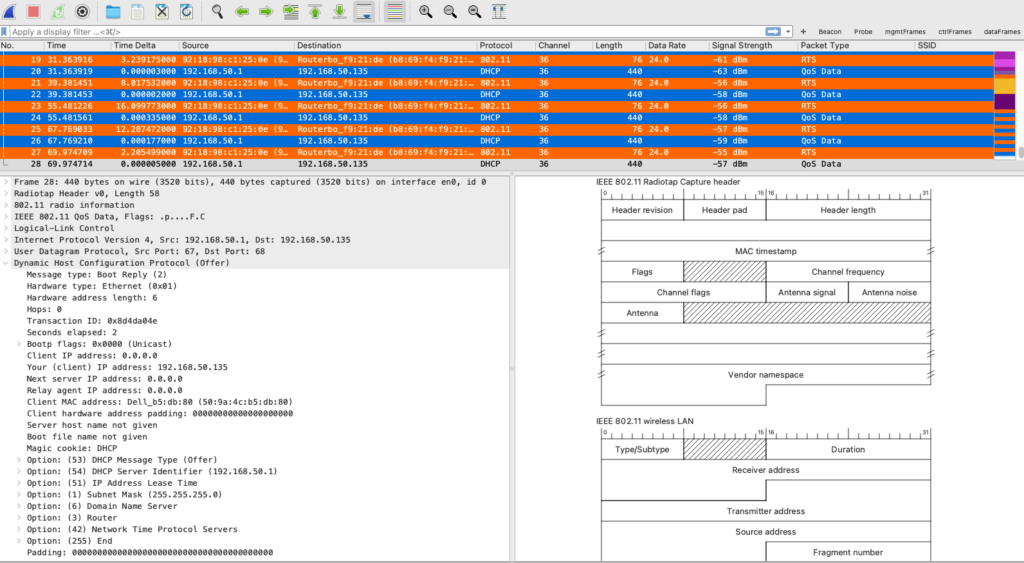
You can see the entire payload which includes a DHCP offer.
In conclusion, decrypting 802.11 frames could be very helpful in a troubleshooting session, instead of seeing only the 802.11 protocols, you can see another picture with L3 information on there. For instance; if your supplicant is sending a Discover, and receiving an offer needed.
I hope you find this post useful! Please be safe and take care of yourself!